The security of map and data is one of the biggest stumbling block an organization can face when making the transition to a web based mapping system. In this article I will show you how to overcome this obstacle.
Moving from having maps and data available on a local network to the web feels like a huge leap of faith, especially when using cloud providers. Before making the jump you and decision makes in your organization will need to be confident in versatility the security options available to you.
In this article I’m going to take you through the various levels of security scenarios to consider when moving your maps and data online. You will learn the best practices for map and data security and how to implement them.
We will start from the most open security policies through to the most stringent.
Open Maps, Open Data
This means no security, but I’m including it first so that we can use it as a baseline.
With web mapping there is a difference between making the maps open and making the data open. Maps are made up of tiled images, they are a representation of the data, but not the raw data itself.
Of course if someone was very determined they could digitize the geometry and scrape all the attribute data, but it’s not making it easy for them.
Open data means that we don’t only give access to the map (the representation of the data) we also give access to the raw data in a common format such as Shapefile, GeoTIFF or CSV.
This kind of openness is gaining more and more popularity especially in the government and NPO domain on the back of the growing open data movement.
Open Maps, Closed Data
In this scenario you give users access to the maps (a representation of the data), but not the raw data. You may also choose to restrict which attributes are visible when a user performs a feature selection or a query.
Hidden Maps
These are maps aren’t intended for public consumption but also aren’t sensitive in nature so it’s not the end of the world if they are seen by outsiders. You just don’t want to encourage it.
A hidden map uses what we call a UUID (universal unique identifier) in the URL, which is a 32-character hexadecimal code. A UUID looks like this:
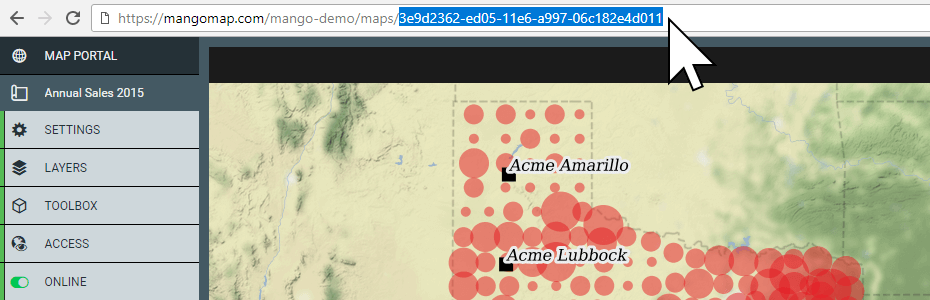
The chances of randomly guessing this code is 1 in 103 trillion.
In addition to the code, the web page containing the map contains a ’noindex’ tag, this tag tells search engines not to add this page to their search result should they find it by chance.
To share a hidden map, you can just share the URL with those that you would like to access the map. But you must be aware that anyone else they share the URL with, will also have access.
Password Protected Maps
Password protection is the simplest form of access restriction. When a user navigates to the map URL they are asked to enter a password in order to gain access
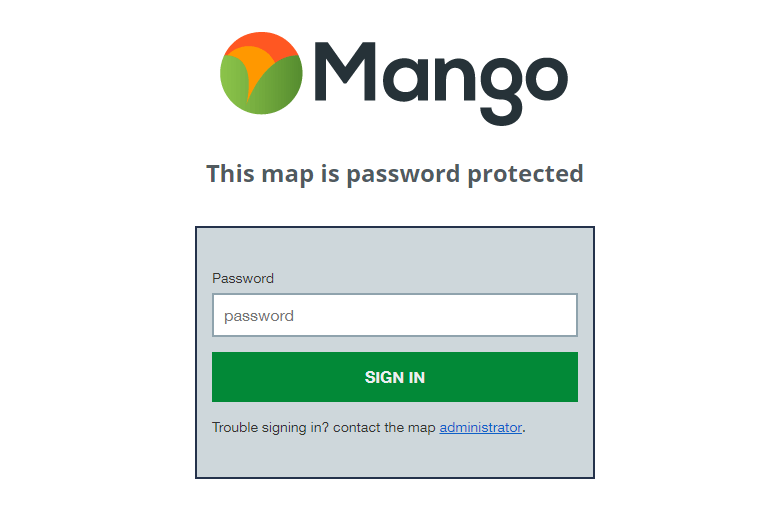
Password protection is slightly more secure than a hidden map, because now if someone stumbles across it by accident they still can’t view it. But just like the hidden map any user with whom you share the password can just as easily share the link and password with anyone of their choosing.
User and Group Based Security
This is the gold standard of web map security. In this case you issue each user login credentials that consist of their email address and a password.
You also create groups. Each group can contain one or more users, then on each map and dataset you can choose what each group is able to do. These are the common options:
- Can only view the map
- Can view the map and download specific datasets
- Can view the map and also edit specific datasets
- Can administer the map and also edit specific datasets
The advantage of using groups is that it’s quick to change the permissions for large numbers of people at the same time and also remove or move users between groups as their role or responsibilities within the organization change.
An added bonus to signed in users is that you can track who accessed, downloaded or edited what, when they did it and what physical location they did it from.
This data can be captured in a log and can be regularly reviewed for suspicious activity in the case of highly sensitive datasets. Suspicious activity might include access from unfamiliar locations or an account that is accessing maps and data with a greater frequency than one might expect.
Web Map Security in Mango
Mango, our cloud based online GIS implements all of the security options outlined above. In addition, all requests are encrypted using 256-bit SSL encryption and our servers are located in one of the most secure data centers in the world.
Please take a moment to watch this short video (1:51) that outlines the benefits of Mango’s security options:
As with all Mango features what you won’t needs is:
- Any programming skills
- A server
- Expensive software licenses