Do you only use your web GIS for public maps? Get more from your web GIS by using it for internal workflows and data sharing.
Local governments tend to view their online GIS as a tool to assist local residents and companies rather than themselves.
In this article I'm going to make the case for getting greater value from your web GIS system by using it as a tool for internal data sharing and work related processes.
The bread and butter of a local government GIS is land record maps, zoning maps, and boundary information, while large volumes of non-public facing map data remain hidden away on the local network.
Before we start, let's step back for a moment and ask ourselves what is the benefit to your users of a web based GIS system?
Of course, the first answer is access to the data. That's correct, but if that was the only value why wouldn't we take the far faster and far cheaper option of simply making the Shapefiles available for download on our website?
A web GIS offers lots of additional benefits:
- Easy to access
- Easy to use
- No software required
- Easily integrated with existing systems
- Easily integrated with existing workflows
These benefits aren't unique to local residents and companies, they are equally beneficial to local government staff and contractors.
But most local governments tend not to utilize their web GIS system for internal work flows or data distribution and instead focus only on publicly accessible maps and data.
As you have likely made a significant time and budget investment in your web GIS it makes sense to maximize that investment by looking for innovative ways to leverage your web GIS system internally.
The two lowest hanging fruits are internal data distribution and map based workflows.
This could mean making non-publicly accessible datasets available to relevant staff and contractors or building web based workflows such as utility management and public works available via the browser or mobile devices.
Before we take a closer look at some use cases let's first think about security, as data security is usually the first objection raised when proposing the sharing of non-public data via a web based system.
Security Levels
With a web GIS system you will usually have three levels of security.
Hidden Maps
A hidden map is the lowest level of security, it's used in cases where the data contained isn't sensitive but you would still rather not advertise the map to residents or have it listed on search engines.
A hidden map works by using an unguessable hash in the URL. A standard map URL might look like this:
https://springfield-county.com/maps/land-records
A map that utilizes a hash would look like this:
https://springfield-county.com/maps/7d8edef8-3abc-11e7-b358-06c182e4d011/land-records
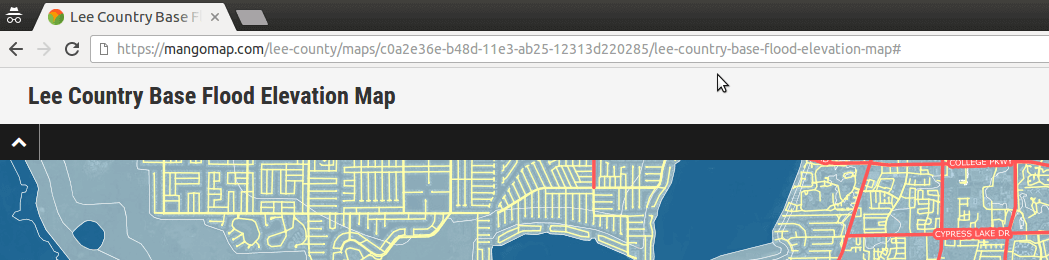
The map would also contain a special instruction in its HTML code that will tell search engines not to list the map in their search results:
<meta name="robots" content="noindex">
A hidden map doesn't offer any real access control, anyone that knows the URL can share it with anyone else. Its real purpose is to prevent others finding it by accident.
Password Protected Maps
One level up in terms of security is a password protected map. A password protected maps will prompt visitors to enter a password before being given access to the map.
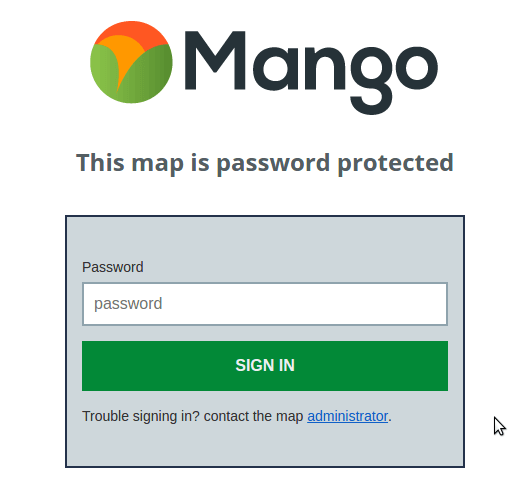
The main benefit of a password protected map is that it offers greater security than a hidden map and is also very easy to setup.
All you need to do is set the password for the map and share that password with the users you wish to grant access, which is in most cases as simple as a mail out to the relevant people.
So the upside is the ease with which the map can be set up and shared.
The downside of the password protected map is that the password can easily be shared and you can't block access for specific users or see who has been accessing the map, this makes it unsuitable for highly sensitive data.
Users, Groups and Access Permissions
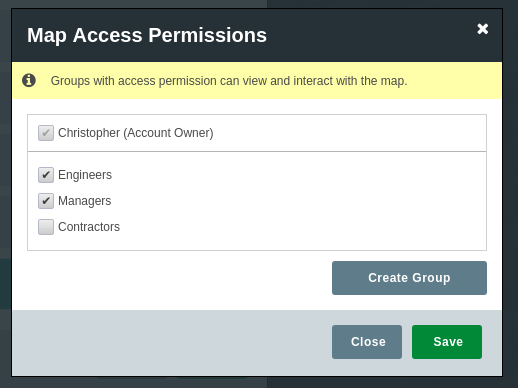
The most robust security solution for your web maps is the creation of additional users that can each be granted specific permissions.
This method allows you to grant access for an individual to specific maps and datasets. But unlike the password protected maps you can also remove access rights for an individual at any time.
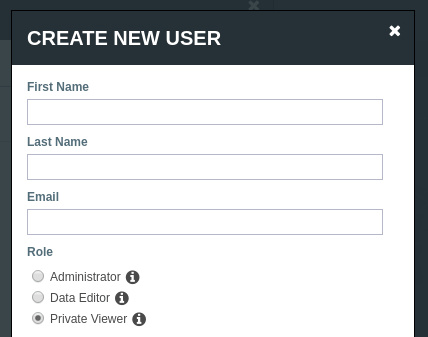
A robust system will also provide groups. A group can be given specific access and editing rights and then any users that are added to the group will inherit the permissions of that group.
This makes it easy to manage large numbers of users as any changes to the group will propagate down to all the users that belong to the group.
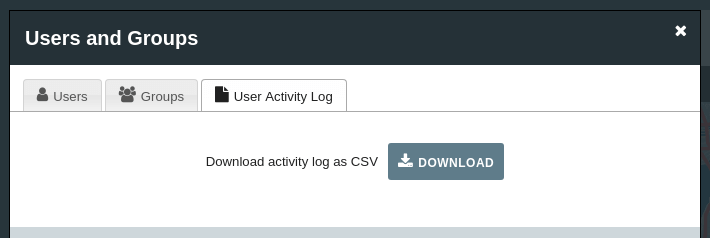
For very sensitive data it is also advisable to make a user activity log available to the site administrators.
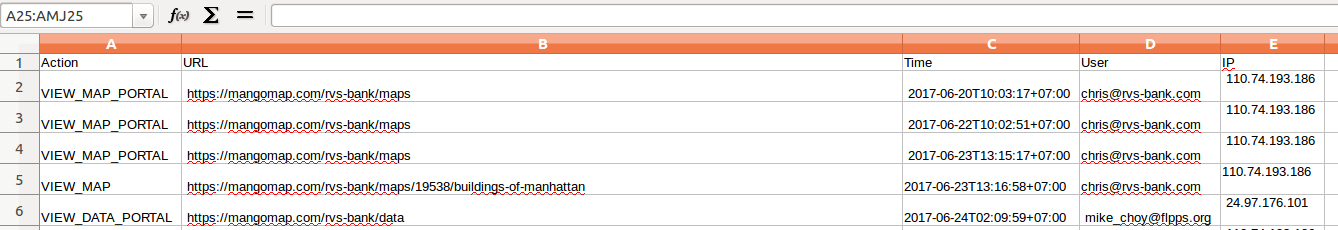
The log, which should be periodically checked for suspicious activity, should contain the name of the user, the map or dataset that was accessed along with a timestamp and their IP address.
Suspicious activity might include:
-
An abnormally high level of activity from a specific user which could indicate that the account is being used by more than one individual
-
Abnormal access times, such as outside of regular business hours
-
Suspicious IP addresses that don't map to the geographical location of known users
Local Government Use Cases
So let's go ahead and take a look at some common use cases for local government that require additional map security and internal sharing options.
Public Works
A common task for cities and towns is the management of public works and utilities.
A web GIS offers a number of benefits for local government and can act as an interactive communication channel between GIS staff, decision makers and maintenance crews.
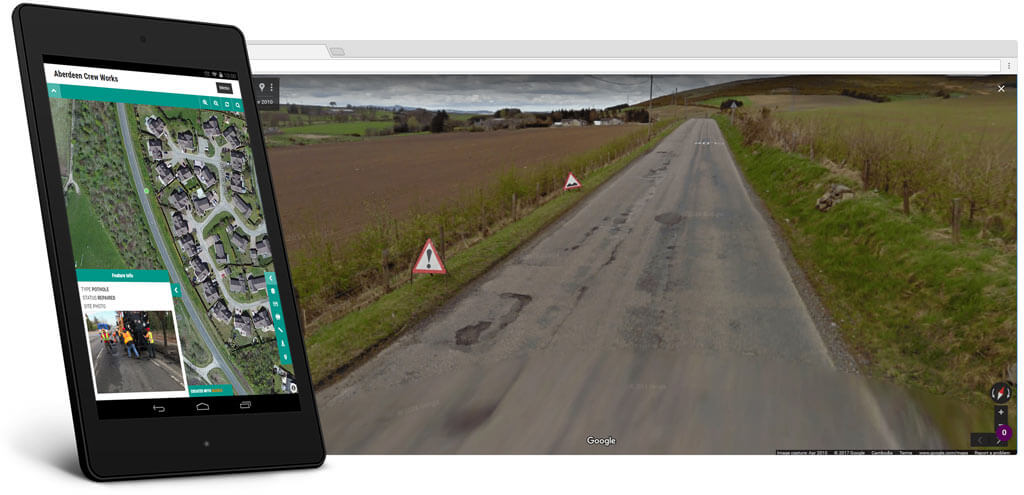
A good example is road repairs. A map can be created that contains the road network and markers for areas that require repair or the locations of previously completed repairs.
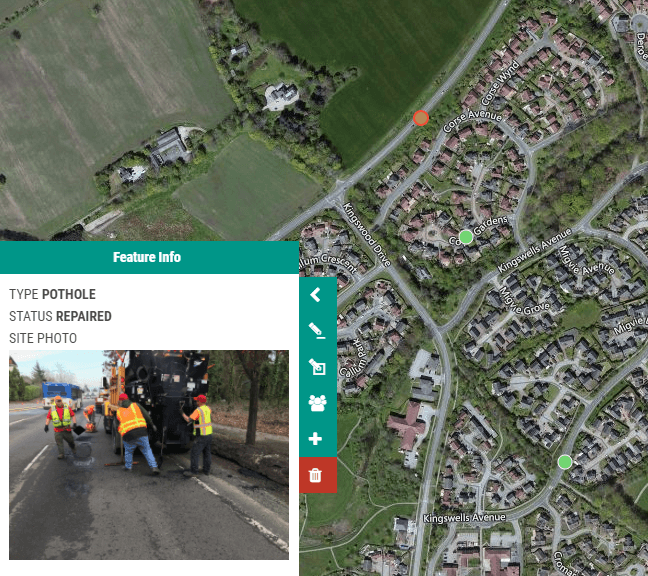
An example workflow might work as follows:
-
Field staff add pothole location and photograph to the map using their mobile device
-
A staff member from public works reviews the submission and sets the priority level
-
Repairs can be reviewed using Google Street View and grouped by location
-
Road repair crews can view potholes that have been scheduled for repair on the map and locate them using the GPS of their mobile device
-
Once the repair is complete the contractor can change the status to complete
This system could utilize users and groups. With the following groups each with their own permissions granting them specific access and editing privileges.
-
Map administrators
-
Public works staff
-
Repair Crew
Utility Mapping
Comprehensive maps of local utilities can be created and shared with relevant staff and contractors.
The maps might include:
-
Water pipes and valves
-
Electricity grid
-
Internet and communications network
Water Pipes and Valves
Power Grid
Different groups could be granted access and edit permissions for the maps which are relevant to their position and role.
Disaster Preparedness Maps
Areas that are prone to flooding and natural disasters can have web GIS maps in place that can be easily shared, updated and utilized during an event.
These could include:
-
Home address and contact details of first responders
-
Location of disaster response assets
-
Reports of incidents during an ongoing event
-
Supplementary data such as FEMA maps
The system should make it easy for access to quickly be granted to online map resources during the chaotic and fast moving conditions of a disaster event.
Maps That Contain Private Information
There are many datasets that contain the personal information of residents or businesses that can't be shared publically but are none the less very useful when made available for relevant staff in a map based format.
An example might be the issue and status of licenses and permits.
In Conclusion
As you can see there is lots of value to be gained from your web GIS system other than public facing maps. Having an online GIS system with a wide range of privacy and security options can open up a whole range of new possibilities for internal data sharing and workflows.